 Before I continue my series on how to image Mac systems, I wanted to cover how to mount and work with FileVault2 encrypted Mac images. By "work with", I mean decrypt it and create an image of the decrypted volume in either raw (dd) or E01 format to pull into X-Ways, EnCase etc. To do this three things are needed:
Before I continue my series on how to image Mac systems, I wanted to cover how to mount and work with FileVault2 encrypted Mac images. By "work with", I mean decrypt it and create an image of the decrypted volume in either raw (dd) or E01 format to pull into X-Ways, EnCase etc. To do this three things are needed:1) A full disk image of the encrypted system in raw format (dd)
2) The SIFT Workstation - it has all the (free!) tools needed already installed
3) The password or recovery key for the volume.
For this example, I am going to use the encrypted disk image of a Mac I created from this previous turotiral. Below is what the encrypted image looks like in FTK Imager. Note that the second partition, MacOSX, is showing as an Unrecognized file system. This is because it is encrypted with FileVault2:
Another way to verify that the partition is encrypted is to look for the EncryptedRoot.plist.wipekey on the Recovery partition. In fact, we are going to need this to decrypt the drive, so I am just going to export out this file while I have it opened in FTK Imager. Mine was located under Recovery HD [HFS+]\Recovery HD\com.apple.boot.P\System\Library\Caches\com.apple.corestorage\EncryptedRoot.plist.wipekey:
If you're using SIFT in a VM, the first step is to create a shared folder(s) for where the image is located, and where you want your decrypted dd/E01 image to go. Here I have two USB drives shared as E: and G:. The E: drive contains my encrypted image and my EncryptedRoot.plist.wipekey file. The G: drive is where I am going to dump the unencrypted image. In Virtual Box these settings were located under Settings > Shared Folders.
Next, I am going to make a mount point to mount the image:
Now I am going to change into the directory where I have my image and wipekey:
Joachim Metz has written a library, libfvde, to access FileVault encrypted volumes. I will be using fvdemount from this library to mount the encrypted partition. He has excellent documentation on his wiki - I will pretty much be following that in the steps below.
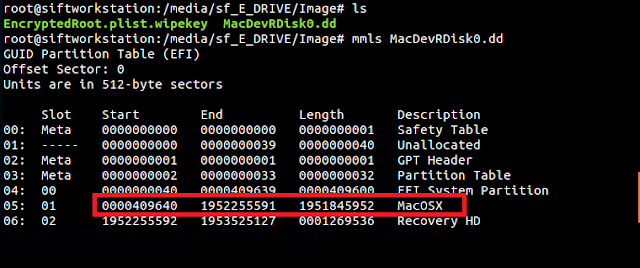
I need to get the partition offset in bytes to pass to fvdemount. mmls from the Sleuth Kit can be used to get the offset from the image:
According to output above, the MacOSX encrypted partition starts at sector 409640. To get the offset in bytes multiply the offset (409640) times 512 bytes / per sector. I will need to pass this offset (-o), the EncryptedRoot.plist.wipekey (-e),the password or recovery key (-p), my image and the mountpoint to fvdemount:
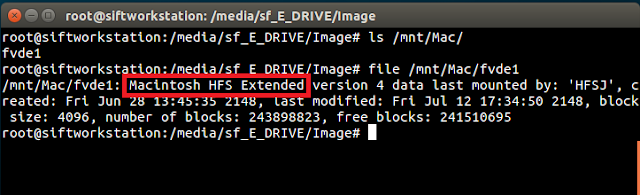
fvdemount will create a device file named "fvde1" under the mount point. A quick file command confirms it is the HFS volume:
To further verify everything is unencrypted, fvde1 can be mounted as a loopback device to show the files system:
As shown above, I can now see the unencrypted Mac partition.
If your preference is to work with an image under Windows with tools like X-Ways, EnCase etc, an image can be taken of the unencrypted device, /mnt/Mac/fvde1.
For E01 format, ewfaquire can be used:
ewfaquire /mnt/Mac/fvde1
For raw (dd) format the following syntax can be used. I like to have a progress bar so I am using using the pv command with dd. For dd, I am using the recommend parameters from the Forensic Wiki.
dd if=/mnt/Mac/fvde1 bs=4K conv=noerror,sync | pv -s 999345127424 | dd of=/media/sf_G_Drive/Image/Mac_fvdemount_unencrypted.dd
-s is the size, which can be taken from the length of the partition, 1951845925 sectors * 512 bytes/sector = 999345113600 bytes (aprox. 1TB)
After the image completes, it can now be be opened and viewed in all it's unencrypted glory in the tool of your choice:
A Mac system can also be used to mount an encrypted volume. I may write a post about that at a later time. I know not all examiners have access to a Mac system, so I wanted to focus on this method first. Plus, I like good 'Ol Tux.









Please tell us how to mount an encrypted volume .E01 format on MacOS...i really need some help. I have an external HD encrypted with all my files to recover and i do not know how to do it...
ReplyDeleteTry to use xmount
Deletexmount --in ewf --out dd MAC_FC.E* /mnt/raw/
Jose,
ReplyDeleteTry converting the E01 image to a dd image (FTK can do this, and I think there are some tools in Linux that can do it as well.) If all you have is a Mac, you can install a free linux distro, like Ubuntu or the SIFT Workstation in Virtual Box and follow the above steps.
hey Mari,
ReplyDeleteThere is a way to access an encrypted removable media?
I didn't find EncryptedRoot.plist.wipekey in the removable media.
I have a FileVault2 encrypted removable media that I want to access from UBUNTU.
thanks